In today’s digital age, passwords remain one of the most crucial elements of cybersecurity. Despite advances in technology, weak or compromised passwords continue to be a leading cause of data breaches and cyberattacks. As we step into 2024, the need for robust password management practices is more important than ever. This guide will delve into the best password management practices for 2024, providing actionable tips to secure your online accounts and personal information.
Why Password Management is Crucial in 2024
The increasing sophistication of cyber threats has made it imperative for individuals and businesses alike to adopt strong password management strategies. Weak passwords, reused across multiple accounts, can open the door to hackers, leading to identity theft, financial loss, and compromised data. As technology evolves, so do the methods used by cybercriminals, making it essential to stay ahead of the curve with up-to-date password practices.
The Importance of Strong, Unique Passwords
1. Characteristics of a Strong Password
A strong password is the first line of defense against unauthorized access. As of 2024, a strong password should:
- Be at least 12-16 characters long.
- Include a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid easily guessable information, such as names, birthdates, or common phrases.
2. The Dangers of Password Reuse
Reusing passwords across multiple accounts is a common but dangerous practice. If one account is compromised, it can lead to a domino effect where all accounts using the same password are at risk. Always ensure each account has a unique password.
3. Passphrases: A New Standard
Passphrases, which are longer and easier to remember than traditional passwords, are becoming increasingly popular. A passphrase could be a combination of random words, such as “MountainBlueRiver2024!”, which is both strong and memorable.

Password Managers: Your Digital Security Vault
1. Why Use a Password Manager?
Password managers are essential tools for managing and securing multiple passwords. They store your passwords in an encrypted vault, allowing you to generate and use strong, unique passwords without the need to remember them all.
2. Top Password Managers for 2024
Several password managers have stood out in 2024 for their security features and ease of use. Some of the best options include:
- LastPass: Offers a user-friendly interface and robust security features.
- 1Password: Known for its security and ability to store more than just passwords.
- Dashlane: Provides a secure and intuitive platform with additional features like VPN access.
3. How to Use a Password Manager Effectively
To get the most out of a password manager:
- Use it to generate strong, unique passwords for each account.
- Enable two-factor authentication (2FA) on the password manager itself for added security.
- Regularly update and review the stored passwords to ensure they remain secure.
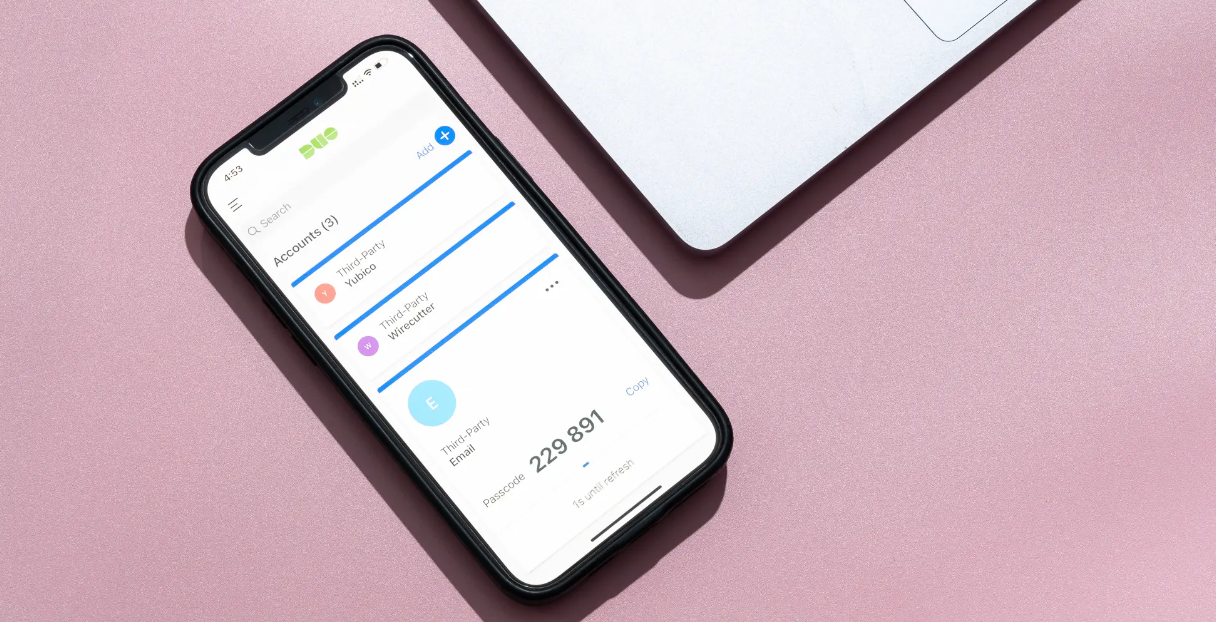
Two-Factor Authentication (2FA): Adding an Extra Layer of Security
1. What is Two-Factor Authentication?
Two-factor authentication (2FA) is an additional layer of security that requires not just a password but also a second form of verification, such as a code sent to your phone or an authentication app.
2. Types of Two-Factor Authentication
- SMS-based 2FA: A code is sent via SMS to your phone.
- Authenticator Apps: Apps like Google Authenticator or Authy generate time-based codes.
- Biometric Verification: Use of fingerprint or facial recognition as a second factor.
3. Best Practices for Using 2FA
- Always enable 2FA for critical accounts, such as email, banking, and social media.
- Prefer authenticator apps over SMS-based 2FA, as they are more secure against SIM-swapping attacks.
- Regularly review and update your 2FA settings to ensure they remain effective.
Regularly Updating and Reviewing Passwords
1. Why Regular Password Updates are Necessary
Cybersecurity experts recommend changing your passwords regularly, especially if you suspect any account may have been compromised. Regular updates can prevent potential breaches and keep your accounts secure.
2. Setting Up a Password Update Schedule
- Critical Accounts: Update passwords every 3-6 months.
- Less Critical Accounts: Update passwords annually or biannually.
- Use a password manager to remind you of scheduled updates.
3. How to Identify Compromised Passwords
- Regularly check for any suspicious activity in your accounts.
- Use tools like “Have I Been Pwned” to see if your email or passwords have been involved in a data breach.
- If you receive notifications about password resets you didn’t initiate, change your passwords immediately.
Avoiding Common Password Pitfalls
1. Avoiding Common and Easily Guessable Passwords
Passwords like “123456,” “password,” and “qwerty” are still among the most commonly used and are highly vulnerable to attacks. Always avoid using such easily guessable passwords.
2. Don’t Share Your Passwords
Sharing passwords, even with trusted friends or family, can compromise your security. If you must share access, use password manager features like sharing vaults, which provide controlled and secure access.
3. Public Wi-Fi and Password Safety
Avoid entering passwords when connected to public Wi-Fi networks, as these can be easily compromised. If necessary, use a VPN to encrypt your connection.
Image Placeholder: A warning sign on a public Wi-Fi network indicating potential security risks.
Alt Text: “Public Wi-Fi warning sign alerting users to potential security risks when entering passwords.”
The Role of Biometrics in Password Management

1. Biometric Authentication Explained
Biometric authentication uses unique physical characteristics, such as fingerprints or facial recognition, to verify your identity. It is increasingly being integrated into password management for enhanced security.
2. Advantages and Limitations
- Advantages: Biometrics are difficult to replicate, providing a high level of security.
- Limitations: While secure, biometric data is sensitive, and if compromised, it cannot be changed like a password.
3. Integrating Biometrics with Password Management
Many modern devices allow you to combine biometrics with traditional passwords for multi-factor authentication, adding an extra layer of security.
Protecting Your Passwords from Phishing Attacks
1. Recognizing Phishing Attempts
Phishing attacks often involve fraudulent emails or messages designed to trick you into revealing your passwords. Always be cautious of unsolicited messages that ask for login credentials or personal information.
2. Using Anti-Phishing Tools
Consider using browser extensions or antivirus software with built-in anti-phishing features to block malicious websites and alerts on suspicious activities.
3. Educating Yourself and Your Team
Regularly educate yourself and your team about the latest phishing tactics and how to avoid falling victim to them. Being aware of the common red flags can prevent most phishing attempts from being successful.
Conclusion: Staying Ahead with Password Management Best Practices in 2024
As cyber threats continue to evolve, so must our approach to password management. By adopting the best practices outlined in this guide, you can significantly enhance your digital security and protect your sensitive information in 2024 and beyond. Remember, password management is not just about creating strong passwords but also about staying vigilant, using the right tools, and regularly updating your security measures.
Final Thoughts: Security is an ongoing process. Regularly review and update your practices to adapt to new threats and technological advancements. By staying informed and proactive, you can protect your digital life effectively.

