In today’s digital landscape, ransomware attacks have become one of the most destructive cyber threats. These attacks involve malicious software that encrypts a victim’s files, rendering them inaccessible until a ransom is paid. Ransomware targets all types of entities, from individuals to large corporations and governments. Understanding how to detect and prevent ransomware is critical to maintaining cybersecurity.
In this article, we’ll explore the key strategies for detecting and preventing ransomware attacks, covering both technical and practical methods.
What is Ransomware?
Ransomware is a form of malware that encrypts files on a victim’s system, often locking them out until a ransom is paid, typically in cryptocurrency. It can infiltrate systems through phishing emails, malicious downloads, or exploiting vulnerabilities in unpatched software.
Types of Ransomware
There are various types of ransomware, each with distinct methods of operation:
- Crypto Ransomware: This type encrypts the user’s files, making them inaccessible without a decryption key.
- Locker Ransomware: It locks the victim out of their device, preventing them from accessing any applications or files.
- Scareware: Fake software that claims to detect issues on the device, scaring the user into paying for unnecessary services or fixes.
- Ransomware as a Service (RaaS): A model where ransomware creators sell their software to attackers, lowering the barrier to entry for would-be cybercriminals.
How Ransomware Infiltrates Systems
Ransomware spreads through various attack vectors, including:
- Phishing Emails: The most common method, where victims are tricked into clicking malicious links or downloading infected attachments.
- Drive-by Downloads: This occurs when a user visits a compromised website that automatically downloads malware onto their device without their knowledge.
- Remote Desktop Protocol (RDP) Vulnerabilities: Attackers exploit weak RDP configurations to gain unauthorized access to systems.
- Exploiting Software Vulnerabilities: Outdated or unpatched software can be an easy target for ransomware attacks.
How to Detect Ransomware Attacks
1. Unusual Network Traffic
One of the first signs of ransomware is abnormal network activity. Ransomware often communicates with command-and-control servers to download encryption keys or upload stolen data. Monitoring outbound traffic, especially to known malicious domains, can reveal early signs of an attack.
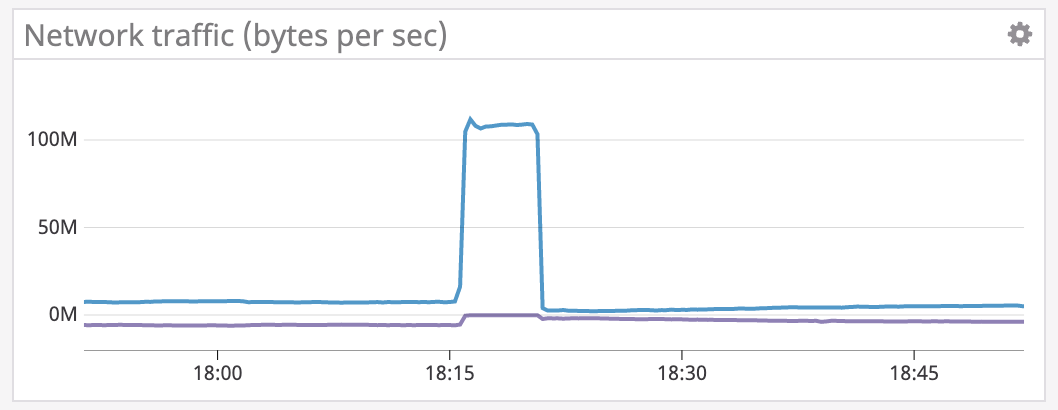
2. Unexpected File Extensions or Encrypted Files
If you notice that file extensions have changed or that files have been encrypted without your knowledge, it is a clear sign of a ransomware attack. The files may have strange extensions like “.locked” or “.crypt.”
3. Slow System Performance
Sudden, unexplained system slowdowns or freezes could be an early warning sign. Many ransomware variants consume significant system resources as they encrypt files, leading to reduced performance.
4. Unauthorized Access or Privilege Escalation
Keep an eye on any unauthorized access to sensitive files or unusual changes in user privileges. Ransomware attackers often escalate their privileges to gain access to more critical areas of the system.
5. Ransom Note or Pop-up Demands
This is usually the most obvious sign of a ransomware attack: receiving a ransom note demanding payment to regain access to your files. The message might appear as a pop-up or in a text file.
How to Prevent Ransomware Attacks
1. Implement Strong Email Security
As phishing remains the primary delivery method for ransomware, improving email security is critical. Use email filtering tools that block suspicious attachments and URLs, and educate employees on how to spot phishing attempts.

2. Regularly Back Up Your Data
Backing up your files regularly is one of the most effective ways to mitigate the damage caused by ransomware. Store backups offline or in secure cloud environments, ensuring they’re inaccessible to any ransomware infection on your system.
3. Keep Software Updated and Patched
Regularly updating your software and applying security patches is essential for closing vulnerabilities that ransomware may exploit. Enable automatic updates where possible to ensure that your systems remain protected.
4. Use Multi-Factor Authentication (MFA)
Using MFA adds an extra layer of protection by requiring users to verify their identity through multiple means, making it harder for ransomware attackers to gain access to sensitive areas of your network.
5. Deploy Endpoint Detection and Response (EDR) Tools
EDR tools actively monitor endpoints for suspicious activity, offering real-time detection and mitigation of ransomware threats. These tools can also contain ransomware attacks before they spread to other systems.
6. Educate Employees on Cybersecurity Best Practices
Human error is one of the biggest risks when it comes to ransomware. Training your workforce on cybersecurity best practices, such as identifying phishing emails and avoiding suspicious downloads, can reduce the risk of ransomware infiltrating your systems.
Advanced Ransomware Prevention Techniques
1. Use Network Segmentation
Segmenting your network into smaller sub-networks can limit the spread of ransomware in the event of an attack. If ransomware infects one segment, it won’t automatically spread to the entire network.
2. Implement Zero Trust Security

The Zero Trust model is a proactive approach to security where no entity, inside or outside the network, is trusted by default. Implementing Zero Trust requires constant verification of users and devices, which can help stop ransomware attacks before they start.
3. Enable Threat Intelligence Feeds
Threat intelligence feeds provide up-to-date information about emerging ransomware threats. These feeds can help your security team stay informed about the latest attack techniques and apply defenses before attacks occur.
4. Leverage Artificial Intelligence (AI)
AI-driven security solutions can detect ransomware patterns and anomalies faster than traditional methods. These systems can autonomously block suspicious activities and send alerts to your security team for further investigation.
What to Do if You’re Hit by a Ransomware Attack
- Isolate the Infected Device: Disconnect the infected device from your network immediately to prevent further spread of the ransomware.
- Assess the Damage: Identify the type of ransomware and the extent of the damage it has caused. Consult with cybersecurity experts if necessary.
- Do Not Pay the Ransom: Paying the ransom does not guarantee that you’ll regain access to your files, and it encourages further attacks. Instead, seek professional assistance to recover your data.
- Restore Data from Backups: If you have secure backups, use them to restore your data without paying the ransom.
- Report the Attack: Notify the appropriate authorities and your security team about the ransomware attack. Reporting such incidents helps track down the attackers and prevents future attacks.
Conclusion
Ransomware attacks are increasingly sophisticated, but with the right detection and prevention strategies, you can significantly reduce your risk of becoming a victim. From regular backups and software updates to advanced AI-driven solutions and Zero Trust security, defending against ransomware requires a multi-layered approach. By staying vigilant and proactive, businesses and individuals alike can safeguard their data and operations from the devastating consequences of ransomware.

