In an era where cyber threats are becoming increasingly sophisticated, traditional security models that rely heavily on perimeter defenses are no longer sufficient. Enter Zero Trust Security, a paradigm shift in cybersecurity that fundamentally redefines how organizations protect their digital assets. This comprehensive guide delves into what Zero Trust Security is, its core principles, benefits, implementation strategies, and future trends, ensuring you have a thorough understanding of this essential security framework for 2024.
Introduction
As businesses increasingly migrate to digital platforms, the importance of robust cybersecurity measures cannot be overstated. Traditional security models, which primarily focus on defending the perimeter of an organization’s network, are proving inadequate against modern, sophisticated cyber threats. Zero Trust Security emerges as a revolutionary framework designed to address these evolving challenges by assuming that threats could originate both inside and outside the network. This approach fundamentally changes how organizations perceive and implement security, focusing on continuous verification and strict access controls.
What is Zero Trust Security?
Definition
Zero Trust Security is a cybersecurity model that operates under the principle of “never trust, always verify.” Unlike traditional security frameworks that grant broad access to users and devices within a network, Zero Trust enforces strict identity verification and least privilege access, regardless of the user’s location relative to the network perimeter. This model minimizes the risk of internal and external threats by continuously validating trustworthiness before granting access to resources.
History and Evolution
The concept of Zero Trust Security was first introduced by John Kindervag, a former Forrester Research analyst, in 2010. Kindervag argued that the traditional perimeter-based security model was insufficient in the face of emerging cyber threats, particularly those involving insider threats and advanced persistent threats (APTs). Over the past decade, the Zero Trust model has gained significant traction, evolving with advancements in technology and the increasing complexity of cyber threats. Today, it is recognized as a best practice framework by leading cybersecurity organizations, including the National Institute of Standards and Technology (NIST).
Principles of Zero Trust Security
Zero Trust Security is built upon several core principles that collectively enhance an organization’s security posture. Understanding and implementing these principles is crucial for the successful adoption of Zero Trust.
Never Trust, Always Verify
At the heart of Zero Trust is the idea that no user or device should be automatically trusted, regardless of whether they are inside or outside the network. Every access request is treated as though it originates from an untrusted source, necessitating rigorous verification before granting access to resources.
Least Privilege Access
Zero Trust mandates that users are granted the minimum level of access necessary to perform their tasks. This principle limits the potential damage from compromised accounts by ensuring that users only have access to the resources essential for their roles.
Micro-Segmentation
Micro-segmentation involves dividing the network into smaller, isolated segments, each with its own access controls and security policies. This containment strategy prevents lateral movement by attackers within the network, reducing the likelihood of widespread breaches.
Continuous Monitoring and Validation
Zero Trust emphasizes the importance of ongoing monitoring and validation of all network activities. Continuous assessment ensures that any deviations or suspicious behaviors are detected and addressed promptly, maintaining a secure environment.
Benefits of Zero Trust Security
Implementing Zero Trust Security offers numerous advantages that enhance an organization’s overall security posture and operational efficiency.
Enhanced Security Posture
Zero Trust significantly strengthens an organization’s defense mechanisms by enforcing strict access controls and continuous verification. This proactive approach minimizes the risk of unauthorized access and data breaches, safeguarding critical assets.
Reduced Risk of Data Breaches
By limiting access to only what is necessary and isolating network segments, Zero Trust reduces the likelihood of data breaches. Even if an attacker gains access to one part of the network, the impact is contained, preventing them from moving laterally to access other sensitive areas.
Improved Compliance
Many industries are subject to stringent regulatory requirements concerning data protection and cybersecurity. Zero Trust helps organizations meet these compliance standards by implementing robust access controls, encryption, and continuous monitoring, thereby avoiding penalties and enhancing reputation.
Greater Visibility and Control
Zero Trust provides comprehensive visibility into all network activities, enabling organizations to monitor and manage access effectively. This heightened oversight allows for better detection of anomalies and quicker response to potential threats.

Implementing Zero Trust Security
Adopting Zero Trust Security requires a strategic approach that involves assessing current security measures, defining critical assets, and implementing robust access controls. Below are the key steps to successfully implement Zero Trust.
Assess Current Security Posture
Before implementing Zero Trust, it is essential to evaluate the existing security infrastructure. This assessment helps identify vulnerabilities, understand current access controls, and determine the areas that require strengthening.
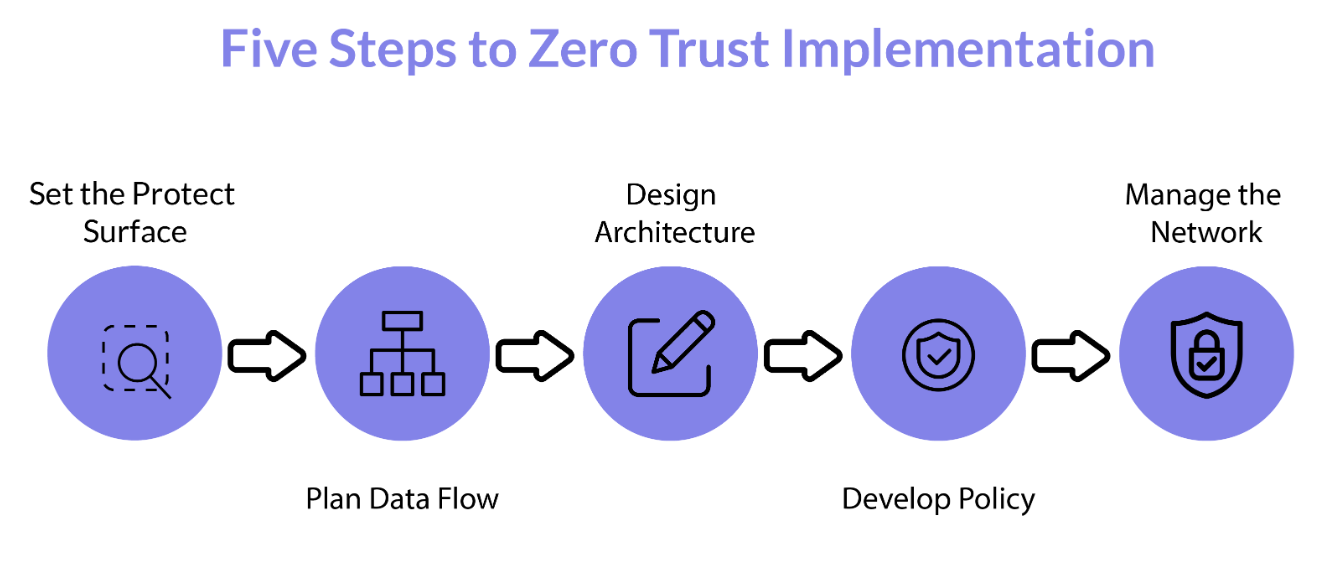
Define Protect Surface
Identify the most critical assets that need protection. These can include sensitive data, applications, and systems. Defining the protect surface helps in focusing security efforts on the areas that are most valuable and vulnerable.
Map Transaction Flows
Understand how data and transactions flow across the network. Mapping these flows is crucial for implementing micro-segmentation and ensuring that access controls are appropriately applied to prevent unauthorized movements within the network.
Architect a Zero Trust Network
Design the network architecture based on Zero Trust principles. This involves implementing micro-segmentation, deploying robust identity and access management (IAM) systems, and ensuring that all components of the network adhere to the Zero Trust model.
Create Zero Trust Policies
Develop and enforce security policies that align with Zero Trust principles. These policies should govern user access, device security, data protection, and incident response, ensuring consistent and comprehensive security measures across the organization.
Monitor and Maintain
Zero Trust is not a one-time implementation but an ongoing process. Continuous monitoring, regular audits, and timely updates are essential to maintain the integrity of the security framework and adapt to emerging threats.
Zero Trust Security vs Traditional Security Models
Understanding the differences between Zero Trust and traditional security models highlights the advantages of adopting a Zero Trust approach.
Perimeter-Based Security
Traditional security models focus on establishing a strong perimeter defense, assuming that everything inside the network is trustworthy and everything outside is not. This approach is akin to building a castle with moats and walls, relying heavily on boundary defenses to keep threats at bay.
Comparison of Effectiveness
While perimeter-based security can be effective in protecting against external threats, it is less effective against insider threats and sophisticated attacks that can bypass the perimeter defenses. Zero Trust, on the other hand, provides a more granular and resilient security framework by continuously verifying and limiting access based on the principle of least privilege.
a comprehensive comparison chart between Zero Trust and Traditional Perimeter-Based Security models:
| Feature | Traditional Perimeter-Based Security | Zero Trust Security |
|---|---|---|
| Trust Model | Implicit Trust Inside the Perimeter Assumes that entities inside the network are trusted by default. | Never Trust, Always Verify Assumes no implicit trust; every access request is authenticated and authorized. |
| Access Control | Network-Centric Primarily based on IP addresses and network locations. | Identity and Context-Centric Based on user identities, device health, and context of the request. |
| Authentication | Basic Authentication Often relies on perimeter defenses like firewalls. | Multi-Factor Authentication (MFA) Strong, continuous authentication mechanisms are enforced. |
| Authorization | One-Time Authorization Grants broad access once inside the perimeter. | Least Privilege Access Granular, just-in-time access based on need and context. |
| Network Segmentation | Limited Segmentation Often relies on VLANs and basic network segmentation. | Micro-Segmentation Highly granular segmentation to isolate resources and limit lateral movement. |
| Visibility and Monitoring | Perimeter Monitoring Focuses on monitoring traffic crossing the network boundary. | Comprehensive Monitoring Continuous monitoring of all user and device activities within the network. |
| Response to Threats | Reactive Responds to threats detected at the perimeter, potentially after breach. | Proactive and Adaptive Detects and responds to threats in real-time, minimizing potential damage. |
| Assumed Trust Levels | High Trust Inside Assumes internal network entities are trustworthy. | Zero Trust by Default No entity is trusted by default, regardless of location. |
| Scalability | Less Scalable for Modern Environments Challenges with cloud and remote work environments. | Highly Scalable Designed to support cloud, remote work, and dynamic environments effectively. |
| Implementation Complexity | Simpler Initial Setup Establishing a perimeter can be straightforward initially. | More Complex Deployment Requires comprehensive planning, integration, and ongoing management. |
| Cost | Potentially Lower Initial Costs May require fewer advanced technologies initially. | Higher Initial Investment Involves costs related to advanced technologies and continuous management. |
| Adaptability | Less Adaptive to Modern Threats Struggles with mobile, IoT, and cloud-based resources. | Highly Adaptive Designed to handle diverse and evolving resources and threat landscapes. |
| User Experience | Potentially Restricted for Internal Users Internal users may face limitations or lack of flexibility. | Enhanced User Experience Provides secure access without unnecessary restrictions, improving productivity. |
| Data Protection | Perimeter-Focused Protection centered around keeping data within the network perimeter. | Data-Centric Protects data wherever it resides, using encryption and strict access controls. |
Key Takeaways
- Traditional Perimeter-Based Security relies on defending the network’s boundary, assuming that threats originate outside and that internal users and devices are trustworthy. This model can be less effective in today’s environment where resources are distributed across cloud services, remote locations, and mobile devices.
- Zero Trust Security operates on the principle of “never trust, always verify,” ensuring that every access request is authenticated, authorized, and encrypted. It emphasizes continuous verification, granular access controls, and comprehensive monitoring, making it better suited to handle modern security challenges.
Implementing a Zero Trust model can significantly enhance an organization’s security posture, especially in environments with high mobility, cloud integration, and a need for robust protection against sophisticated threats. However, it requires careful planning, investment in appropriate technologies, and a cultural shift towards prioritizing security at every level.
Challenges in Adopting Zero Trust
While Zero Trust offers significant security benefits, its implementation can pose several challenges that organizations need to address.
Complexity of Implementation
Transitioning to a Zero Trust model involves overhauling existing security infrastructure and processes. This complexity can be daunting, especially for organizations with limited resources or expertise in cybersecurity.
Cost Considerations
Implementing Zero Trust may require significant investment in new technologies, training, and ongoing maintenance. For smaller organizations, the cost can be a barrier to adoption, necessitating careful planning and resource allocation.
Cultural Shift within Organization
Zero Trust requires a fundamental change in how security is perceived and managed within an organization. Employees must embrace new security practices and understand the importance of continuous verification and strict access controls, which can be challenging to achieve.
Best Practices for Zero Trust Security
To maximize the effectiveness of Zero Trust Security, organizations should adhere to best practices that reinforce the core principles of the model.
Strong Identity and Access Management
Effective Identity and Access Management (IAM) is crucial for implementing Zero Trust. This involves:
- Multi-Factor Authentication (MFA): Adding an extra layer of security by requiring multiple forms of verification.
- Role-Based Access Control (RBAC): Assigning access rights based on users’ roles within the organization.
- Continuous Authentication: Regularly verifying user identities even after initial login to ensure ongoing trustworthiness.
Encryption of Data
Encrypting data both at rest and in transit is essential for protecting sensitive information. Encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties.
- Data at Rest: Use strong encryption protocols to secure stored data.
- Data in Transit: Implement secure communication channels using protocols like TLS (Transport Layer Security).
Endpoint Security
Securing endpoints—such as laptops, smartphones, and IoT devices—is critical in a Zero Trust environment. This involves:
- Endpoint Detection and Response (EDR): Tools that monitor and respond to threats on endpoints in real-time.
- Regular Patching and Updates: Ensuring that all devices are up-to-date with the latest security patches and software updates.
- Device Compliance: Enforcing policies that require devices to meet security standards before granting access to network resources.

Regular Audits and Assessments
Conducting regular security audits and assessments helps identify vulnerabilities and ensure compliance with Zero Trust policies. These audits should cover:
- Access Controls: Reviewing who has access to what resources and adjusting as necessary.
- Policy Enforcement: Ensuring that security policies are being followed and are effective.
- Incident Response: Evaluating the organization’s ability to respond to security incidents promptly and effectively.
Future of Zero Trust Security
As cyber threats continue to evolve, so too will the strategies and technologies used to counter them. Zero Trust Security is poised to integrate with emerging technologies and adapt to new challenges, ensuring its relevance in the future cybersecurity landscape.
Integration with AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are set to play pivotal roles in enhancing Zero Trust Security. These technologies can analyze vast amounts of data in real-time to identify patterns and anomalies that may indicate a security threat.
- Predictive Analytics: AI can predict potential security breaches by analyzing historical data and identifying trends.
- Automated Threat Detection: ML algorithms can detect and respond to threats more quickly and accurately than traditional methods.
Zero Trust in Cloud Environments
With the increasing adoption of cloud services, Zero Trust principles are becoming integral to securing cloud environments. Cloud providers are incorporating Zero Trust frameworks to protect data and applications hosted on their platforms.
- Cloud Access Security Brokers (CASBs): Tools that enforce Zero Trust policies across cloud services.
- Identity Federation: Integrating cloud services with centralized IAM systems to maintain consistent access controls.
Evolving Standards and Frameworks
The Zero Trust model is continuously evolving, with new standards and frameworks emerging to guide its implementation. Organizations are expected to adopt these evolving guidelines to maintain robust security postures.
- NIST Zero Trust Framework: Provides comprehensive guidelines for implementing Zero Trust across different sectors.
- Industry-Specific Standards: Tailored Zero Trust frameworks for specific industries, such as healthcare and finance, addressing unique security requirements.
Case Studies: Successful Zero Trust Implementations
Examining real-world examples of Zero Trust Security implementation provides valuable insights into its practical applications and benefits.
Example 1: Healthcare Sector
A leading healthcare provider implemented Zero Trust Security to protect sensitive patient data and comply with stringent regulatory requirements. By adopting strong IAM practices, micro-segmentation, and continuous monitoring, the organization significantly reduced the risk of data breaches and enhanced overall security.

Example 2: Financial Services
A major financial institution adopted Zero Trust principles to safeguard financial transactions and customer data. Implementing Zero Trust allowed the bank to enforce strict access controls, monitor transactions in real-time, and respond swiftly to any suspicious activities, thereby maintaining customer trust and regulatory compliance.
Image Placeholder: Financial analysts working on secure banking systems.
Alt Text: “Financial analysts operating within a secure Zero Trust environment to protect customer data.”
Conclusion
Zero Trust Security represents a transformative approach to cybersecurity, prioritizing continuous verification and strict access controls to protect digital assets in an increasingly complex threat landscape. By embracing the core principles of Zero Trust—never trust, always verify; least privilege access; micro-segmentation; and continuous monitoring—organizations can significantly enhance their security posture, reduce the risk of data breaches, and ensure compliance with industry regulations.
Implementing Zero Trust requires a strategic and comprehensive approach, addressing various aspects of cybersecurity from identity management to endpoint protection. While challenges such as implementation complexity and cost considerations exist, the long-term benefits of a robust Zero Trust framework far outweigh the initial hurdles.
As we look to the future, Zero Trust Security will continue to evolve, integrating with emerging technologies like AI and machine learning, adapting to cloud environments, and aligning with evolving standards and frameworks. By staying informed and proactive, organizations can leverage Zero Trust to navigate the ever-changing cybersecurity landscape with confidence and resilience.

